|
|
| VPN
Information |
|
What is a VPN?
A virtual private network (VPN) is
the extension of a private network that encompasses
links across shared or public networks like
the Internet. With a VPN, you can send data
between two computers across a shared or public
network in a manner that emulates a point-to-point
private link. Virtual private networking is
the act of creating and configuring a virtual
private network.
To emulate a point-to-point link, data is encapsulated,
or wrapped, with a header that provides routing
information, which allows the data to traverse
the shared or public network to reach its endpoint.
To emulate a private link, the data is encrypted
for confidentiality. Data that is intercepted
on the shared or public network is indecipherable
without the encryption keys. The link in which
the private data is encapsulated and encrypted
is a VPN connection.
VPN connections allow users who work at home
or travel to obtain a remote access connection
to an organization server using the infrastructure
provided by a public network such as the Internet.
From the user's perspective, the VPN is a point-to-point
connection between the computer, the VPN client,
and an organization server (the VPN server).
The exact infrastructure of the shared or public
network is irrelevant, because it appears as
if the data is sent over a dedicated private
link.
VPN connections also allow organizations to
have routed connections with other organizations
over a public network, such as the Internet,
while maintaining secure communications (for
example, between offices that are geographically
separate). A routed VPN connection across the
Internet logically operates as a dedicated wide
area network (WAN) link.
[Return to
top] |
VPN Connection
Types
There are two types of VPN connections:
Remote access VPN connection
Site-to-site VPN connection
Remote access VPN connection
A remote access client makes a remote
access VPN connection that connects to a private
network. VPN Server provides access to the
entire network to which it is attached, allow
the user access to the normal resource that
they would have if they where in the office.
Site-to-site VPN connection
A router makes a site-to-site VPN connection
that connects two portions of a private network.
Site-to-site VPN connections are discussed
in this document. A detailed description of
a hub-spoke or mesh VPN please click on one
of the following links.
Hub-spoke
VPN
Mesh
VPN
[Return to
top] |
VPN
Protocols
There are three VPN protocols for site-to-site
connections:
Point-to-Point Tunneling
Protocol (PPTP)
Layer Two Tunneling Protocol (L2TP) over Internet
Protocol security (IPsec)
Internet Protocol security (IPsec) tunnel
mode
PPTP
Point-to-Point Tunneling Protocol (PPTP) is
a network protocol that enables the secure
transfer of data from a remote client to a
private enterprise server by creating a VPN
across TCP/IP-based data networks. PPTP supports
on-demand, multi-protocol, virtual private
networking over public networks such as the
Internet. PPTP allows IP traffic to be encrypted,
and then encapsulated in an IP header to be
sent across a corporate IP network or a public
IP network such as the Internet.
L2TP over IPsec
Layer Two Tunneling Protocol (L2TP) is an
industry-standard Internet tunneling protocol
that provides encapsulation for sending Point-to-Point
Protocol (PPP) frames across packet-oriented
media. L2TP allows IP traffic to be encrypted,
and then sent over any medium that supports
point-to-point datagram delivery, such as
IP. The Microsoft implementation of the L2TP
protocol uses Internet Protocol security (IPsec)
encryption to protect the data stream from
the VPN client to the VPN server. IPsec tunnel
mode allows IP packets to be encrypted, and
then encapsulated in an IP header to be sent
across a corporate IP network or a public
IP network such as the Internet.
IPsec
When Internet Protocol security (IPsec) is
used in tunnel mode, IPsec itself provides
encapsulation for IP traffic only. The primary
reason for using IPsec tunnel mode is interoperability
with other routers, gateways, or end systems
that do not support L2TP over IPsec or PPTP
VPN tunneling.
[Return
to top] |
|
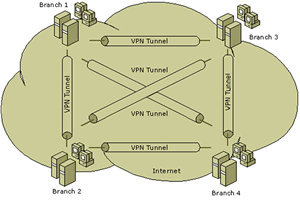
Mesh VPN
In the mesh VPN scenario, each office is
connected to every other office with a VPN connection
as shown in the diagram opposite. There is no
central office.
A mesh VPN configuration can be used when
branch office connectivity to other branch offices
is imperative. The primary drawback of the hub
and spoke VPN is that if the main office network
connection becomes unavailable, connections
between the branch offices are lost. The mesh
VPN solves this problem by connecting all networks
to each other using redundant connections between
branch offices and the main office. Multiple
paths are then available between any two sites.
[Return to
top] |
|
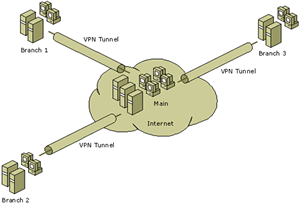
Hub-spoke VPN
In the hub-spoke VPN scenario, each branch
communicates over a VPN connection with the
main office (the hub) and also communicates
with every other branch office (spoke) through
its VPN connection with the hub.
A hub and spoke VPN joins all the branch
offices to the main office. The main office
serves as the hub to which all the branch networks
connect. The branch offices can all connect
to resources on the main office network using
the hub and spoke network connection.
In addition, using a hub and spoke VPN
configuration allows the branch networks to
communicate with one another by sending their
communications through the main office. The
main office then routes these connections to
the appropriate branch office network. This
scenario is shown in the diagram opposite.
[Return to
top] |
|
| |
|
|





